How videos get discovered - gain more youtube views
On YouTube, viewers are matched to the videos they are most likely to watch and enjoy. YouTube’s search and discovery system caters to each viewer...
How do I hide or unhide the number of reactions I see on Facebook posts?
You can hide the total number of reactions you see on ads in News Feed or Facebook posts from other people like family, friends, Pages and groups...
Android and Chrome Users Can Soon Generate Virtual Credit Cards to Protect Real Ones
Every day, google works to create a safer internet by making google products secure by default, private by design, and putting you in control of...

5 Advanced ChatGPT prompt techniques that will put you ahead of the world
Five Advanced ChatGPT prompt techniques that will put you ahead of the world
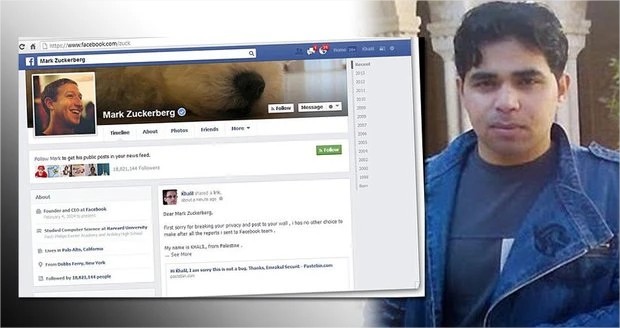
Facebook has begun encrypting links to combat URL stripping that improves privacy
Facebook has started using a different URL scheme for site links to combat URL stripping techniques used by browsers like Firefox or Brave to...
What to Do if an AI-Generated Nude Image or Video of You Is Manipulated and Shared Online
Artificial intelligence (AI) is increasingly being used to manipulate personal images and videos, which are then shared online without consent. This...

How to use the best latest iOS 17 features
iOS 17 is the latest version of Apple's mobile operating system for the iPhone, and it comes with a variety of new features and improvements.
Facebook Disabled Ad Account, How to solve it
To help keep Facebook safe and ensure positive experiences between people and businesses, we review ad accounts to check for violations of our...