Keeping You Safe From Being Hacked

This Article mixed with gathered information from several websites including "Facebook Security Team "
Email is both an excellent communication tool and also a way that companies can inform you about their latest products and services. However, email is frequently used to deliver unwanted material which is at best, annoying and at worst, malicious – causing considerable harm to your computer and yourself.
These include the following:
Spam (or Junk) email
The vast majority of email sent every day is unsolicited junk mail. Examples include:
- Advertising, for example online pharmacies, pornography, dating, gambling.
- Get rich quick and work from home schemes.
- Hoax virus warnings.
- Hoax charity appeals.
- Chain emails which encourage you to forward them to multiple contacts (often to bring ‘good luck’).
How spammers obtain your email address
- Using automated software to generate addresses.
- Enticing people to enter their details on fraudulent websites.
- Hacking into legitimate websites to gather users’ details.
- Buying email lists from other spammers.
- Inviting people to click through to fraudulent websites posing as spam email cancellation services.
- From names/addresses in the cc line, or in the body of emails which have been forwarded and the previous particpants have not been deleted.
The very act of replying to a spam email confirms to spammers that your email address exists.
How to spot spam
Spam emails may feature some of the following warning signs:
- You don’t know the sender.
- Contains misspellings (for example ‘p0rn’ with a zero) designed to fool spam filters.
- Makes an offer that seems too good to be true.
- The subject line and contents do not match.
- Contains an urgent offer end date (for example “Buy now and get 50% off”).
- Contains a request to forward an email to multiple people, and may offer money for doing so.
- Contains a virus warning.
- Contains attachments, which could include .exe files.
The risks
- It can contain viruses and spyware.
- It can be a vehicle for online fraud, such as phishing.
- Unwanted email can contain offensive images.
- Manual filtering and deleting is very time-consuming.
- It takes up space in your inbox.
Email Scams
Examples of email scams include:
- emails offering financial, physical or emotional benefits, which are in reality linked to a wide variety of frauds.
- These include emails posing as being from ‘trusted’ sources such as your bank, the Inland Revenue or anywhere else that you have an online account. They ask you to click on a link and then disclose personal information.
Phising Emails
Phishing is a scam where criminals typically send emails to thousands of people. These emails pretend to come from banks, credit card companies, online shops and auction sites as well as other trusted organisations. They usually try to trick you into going to the site, for example to update your password to avoid your account being suspended. The embedded link in the email itself goes to a website that looks exactly like the real thing but is actually a fake designed to trick victims into entering personal information.
- The email itself can also look as if it comes from a genuine source. Fake emails often (but not always) display some of the following characteristics:
- The sender’s email address is different from the trusted organisation’s website address.
- The email is sent from a completely different address or a free webmail address.
- The email does not use your proper name, but uses a non-specific greeting such as “Dear customer.”
- A sense of urgency; for example the threat that unless you act immediately your account may be closed.
- A prominent website link. These can be forged or seem very similar to the proper address, but even a single character’s difference means a different website.
- A request for personal information such as username, password or bank details.
- You weren't expecting to get an email from the organisation that appears to have sent it.
- The entire text of the email is contained within an image rather than the usual text format. The image contains an embedded link to a bogus site
Attackers are smart than you think , even a medium user of internet would fail against their tricks.
For example , latest weeks attackers start hosting a phishing Gmail page on google drive , a phising page for gmail on the same servers .
Click here for a demo on GMAIL login page : https://googledrive.com/host/0B6FySkkIZwY2SS1PZFNxWW0tRU0/gmail.htm
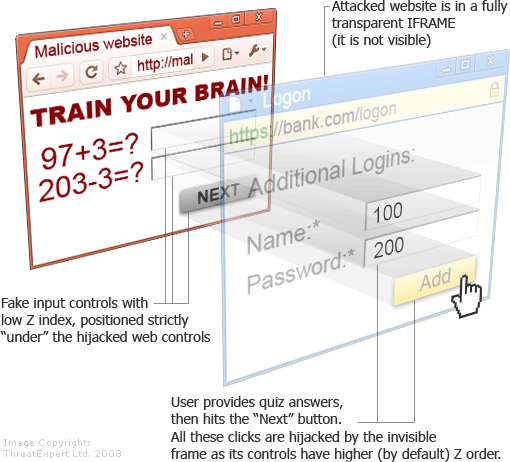
ClickJacking
Spammers sometimes take advantage of a vulnerability in the web browser to try to trick people into clicking on links they might not want to click on. This is called clickjacking, and it’s done by overlaying the link with something more enticing, like a phony offer.
Self-XSS [ Self Cross Site Scripting ]
Spammers take advantage of another browser weakness by asking people to copy and paste malicious code into their address bar, which then causes the browser to take actions on those people’s behalf, Example: Facebook self-xss which let you posting status updates with phony links and sending spam messages to all friends.
Recently every one of you saw a video or image on facebook tells you how to hack your friend account just by copy and paste a code in inspect element, or to change facebook theme , however the code also considered as a scam attack .
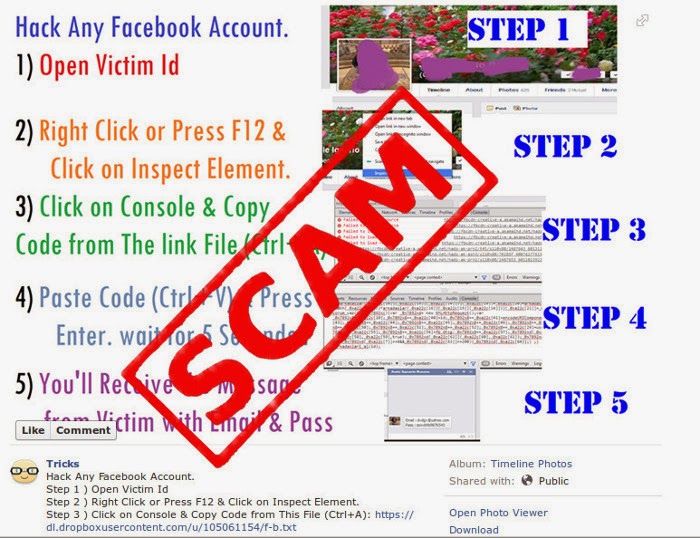
Read More at : http://facebook.com/self-xss
Use email safely
- Do not open emails which you suspect as being spam.
- Do not forward emails which you suspect as being spam.
- Do not open attachments from unknown sources.
- Do not readily click on links in emails from unknown sources. Instead, roll your mouse pointer over the link to reveal its true destination, displayed in the bottom left corner of your screen. Beware if this is different from what is displayed in the text of the link from the email.
- Do not respond to emails from unknown sources.
- Do not make purchases or charity donations in response to spam email.
- Don’t click on ‘remove’ or reply to unwanted email.
- Check junk mail folders regularly in case a legitimate email gets through by mistake.
- When sending emails to multiple recipients, list their addresses in the 'BCC' (blind copy) box instead of in the 'To' box. In this way, no recipient will see the names of the others, and if their addresses fall into the wrong hands there will be less chance of you or anybody else receiving phishing or spam emails.
- Similarly, delete all addresses of previous parties in the email string, before forwarding or replying.
- If you are suspicious of an email, you can check if it is on a list of known spam and scam emails that some internet security vendors such as McAfee and Symantec feature on their websites.
- Most Microsoft and other email clients come with spam filtering as standard. Ensure yours is switched on.
- Most spam and junk filters can be set to allow email to be received from trusted sources, and blocked from untrusted sources.
- When choosing a webmail account such as gmail, Hotmail and Yahoo! Mail, make sure you select one that includes spam filtering and that it remains switched on.
- Most internet security packages include spam blocking. Ensure that yours is up to date and has this feature switched on.
Here are some additional tips you can use to avoid becoming a victim of cyber fraud:
- Do not respond to unsolicited (spam) e-mail.
- Do not click on links contained within an unsolicited e-mail.
- Be cautious of e-mail claiming to contain pictures in attached files; the files may contain viruses. Only open attachments from known senders. Scan the attachments for viruses if possible.
- Avoid filling out forms contained in e-mail messages that ask for personal information.
- Always compare the link in the e-mail to the link you are actually directed to and determine if they match and will lead you to a legitimate site.
- Log on directly to the official website for the business identified in the e-mail instead of “linking” to it from an unsolicited e-mail. If the e-mail appears to be from your bank, credit card issuer, or other company you deal with frequently, your statements or official correspondence from the business will provide the proper contact information.
- Contact the actual business that supposedly sent the e-mail to verify that the e-mail is genuine.
- If you are requested to act quickly or there is an emergency that requires your attention, it may be a scam. Fraudsters create a sense of urgency to get you to act quickly.
- Remember if it looks too good to be true, it probably is.
Advance Thanks For Liking And Sharing
